In cybersecurity, most threats don’t arrive with a headline.
They exploit forgotten systems — a login page on an old domain, a staging app left behind, or a misconfigured port exposed to the internet.
This is not hypothetical.
This case study walks through how a national government agency neutralized a critical exposure using ShieldsGuard’s Attack Surface Management (ASM) — and how this exposure could have resulted in full internal compromise if left unresolved.
The Reality of Public Attack Surfaces
Modern infrastructure evolves rapidly. DevOps teams launch new systems, departments deploy temporary apps, and campaign domains are registered and retired. But what happens when these assets are never properly decommissioned or monitored?
They become invisible liabilities — live, reachable, and exposed.
This is the external attack surface — and for governments, it often spans far beyond what’s documented.
The Incident: An Active, Forgotten Subdomain
Within the first 48 hours of deploying ShieldsGuard ASM, the platform initiated autonomous scans across the agency’s known and shadow infrastructure. The result:
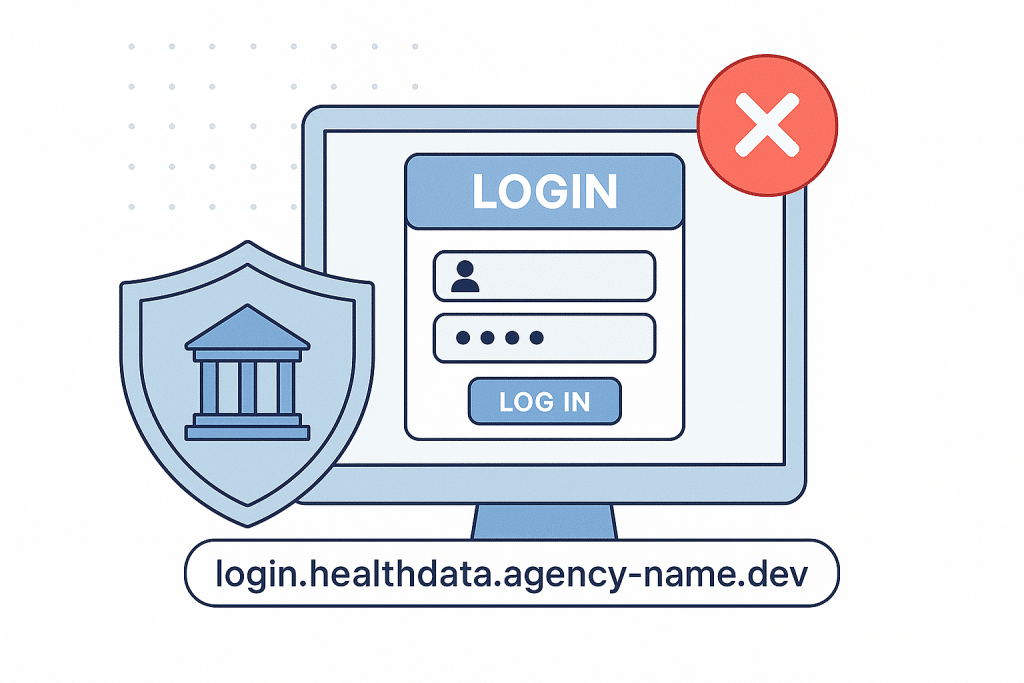
An active login page found at:login.healthdata.agency-name.dev
Key findings:
- DNS records were still live
- TLS certificate had expired, but fallback to HTTP was allowed
- A functioning login form tied to an outdated public health dashboard
- Password reset emails were still triggering to internal addresses
- The asset was not listed in any official inventory
- The subdomain was publicly indexed and visible to external engines

This wasn’t an edge case. It was a critical risk — fully exposed, silently awaiting exploitation.
How ShieldsGuard ASM Responded
Unlike conventional scanners, ShieldsGuard ASM combines continuous discovery with advanced contextual analysis. It doesn’t just check ports — it builds intelligence.

The ASM engine:
- Identified and resolved the subdomain to a live public IP
- Recognized the login interface as a Laravel framework component
- Flagged the expired TLS cert with HTTP fallback as a critical vulnerability
- Correlated the Laravel version with known CVEs, including an auth bypass from 14 months prior
- Scored the asset using real-time exposure, service type, fingerprinting, and discoverability
No intrusive probes. No simulated attacks. Just high-fidelity intelligence generated through passive, continuous monitoring.
The Response: Speed, Integration, Elimination
Upon detection, ShieldsGuard triggered an alert directly into the agency’s SIEM. From that moment:
- The DNS entry was removed
- The backend server was shut down
- The legacy service was deprecated and archived
- The asset was integrated into the central inventory for permanent tracking
No breach. No exploit. No reputation damage.
Only precision — and a closed door.
Why Continuous ASM Is Critical for Governments
Government networks face unique complexity:
- Dispersed departments and disconnected workflows
- Legacy systems managed by rotating teams
- Assets forgotten during policy and personnel changes
ShieldsGuard ASM addresses these challenges with:
- Live subdomain and service discovery
- Full asset fingerprinting across cloud, on-prem, and hybrid networks
- AI-powered misconfiguration and CVE correlation
- Risk scoring that accounts for visibility, service type, and software version
- Exportable, audit-ready reports for internal and external compliance
You don’t need to see everything manually.
You need a system that never stops looking.
Final Thoughts
The asset in this case was minor. Obsolete. Forgotten.
But it was live — and dangerous.
ShieldsGuard ASM didn’t rely on attack simulations or threat signatures.
It delivered real protection through autonomous visibility and intelligent context.
Because in cybersecurity, what you can’t see is exactly what attackers target first.