Cyber threats have become more advanced and faster than ever. While traditional Web Application Firewalls (WAFs) still play a crucial role in detecting known threats, they’re no longer enough. Attackers now exploit business logic flaws, protocol irregularities, and high-volume or malformed requests that standard defenses often miss.
That’s where Security Rules step in. Acting as a pre-WAF filter, solutions like ShieldsGuard use Security Rules to analyze and control requests before they ever reach your core application. From HTTP methods and headers to content-type and JSON bodies, every detail can be used to filter traffic early — keeping threats out before they cause damage.
Understanding the Shift in Web Threats
Web infrastructure is constantly evolving, but attackers often adapt even faster. Modern threats are no longer just about injecting malicious payloads — they’re about abusing logic, overwhelming APIs, and flying under the radar of traditional defenses.
What Are Security Rules and How Do They Work?
Security Rules are proactive filtering mechanisms that allow you to control traffic at the earliest possible stage. Unlike reactive, signature-based defenses, these rules evaluate the behavior of incoming requests — not just their contents.
Key Advantages of Pre-WAF Filtering
By operating before your WAF or application logic, Security Rules offer significant advantages:
- Improved Performance: Malicious traffic is filtered early, reducing load on backend services.
- Granular Precision: Rules can target methods, headers, paths, POST values, or even JSON keys.
Real-World Scenarios Where Security Rules Shine
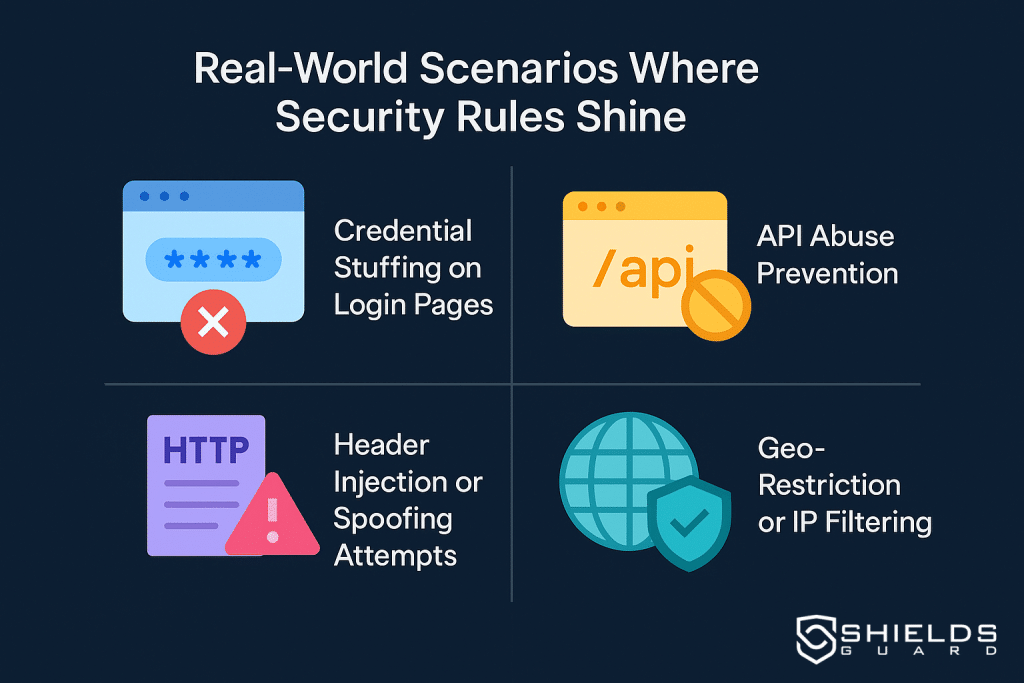
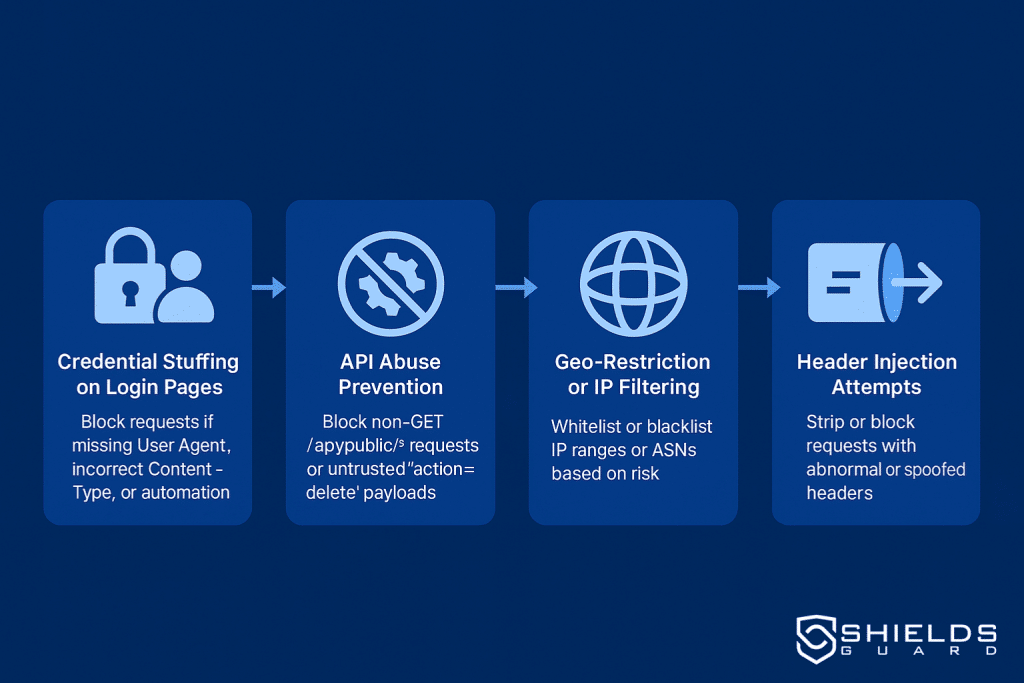
Blocking Credential Stuffing at the Edge
Create rules for /login paths to block requests with missing User-Agent headers, incorrect Content-Types, or known bot patterns in POST data.
Stopping Unwanted API Access in Public Endpoints
Restrict non-GET requests to /api/public/* or allow operations like action=delete only from trusted IPs.
Filtering Malformed or Spoofed HTTP Headers
Reject requests containing manipulated headers like X-Forwarded-For, malformed Referer, or suspicious Host entries.
Using Geo and IP Filtering for Preemptive Protection
Whitelist or blacklist IPs, CIDRs, or ASN origins before your firewall ever sees the request.
ShieldsGuard’s Approach to Security Rules
While many WAF vendors restrict rule customization behind paywalls, ShieldsGuard treats Security Rules as a core feature. Each domain can define its own set of rules — either globally or by specific path — and changes take effect in real-time, with no restarts required.
- Regex pattern matching
- Header, method, and query inspection
- JSON key/value logic
- Detailed logging with match feedback
- Instant rule enforcement
Why Early Filtering Improves Both Security and Performance
Security Rules allow you to take control of your traffic before it hits the WAF. This minimizes server load, reduces false positives, and keeps your applications agile, efficient, and safe.
Conclusion: Control Begins Before the WAF
In a threat landscape defined by speed and complexity, reactive protection is no longer enough. You need control at the edge — and Security Rules make that possible.
At ShieldsGuard, we believe real security begins at the earliest stage of the request lifecycle. That’s why Security Rules are not optional — they’re essential.