In a world where cyberattacks grow more complex by the hour, Distributed Denial of Service (DDoS) attacks remain a persistent and evolving threat. But unlike traditional methods that simply absorb or deflect traffic, ShieldsGuard neutralizes DDoS attacks with precision — using intelligent filtering, real-time logic, and a resilient infrastructure designed for global scalability.
This post highlights real DDoS attempts detected and mitigated by ShieldsGuard — not with brute force, but with the system’s built-in AI-driven defense engine and modular architecture.
Attack #1: Layer 7 Flood with Rotating User-Agents
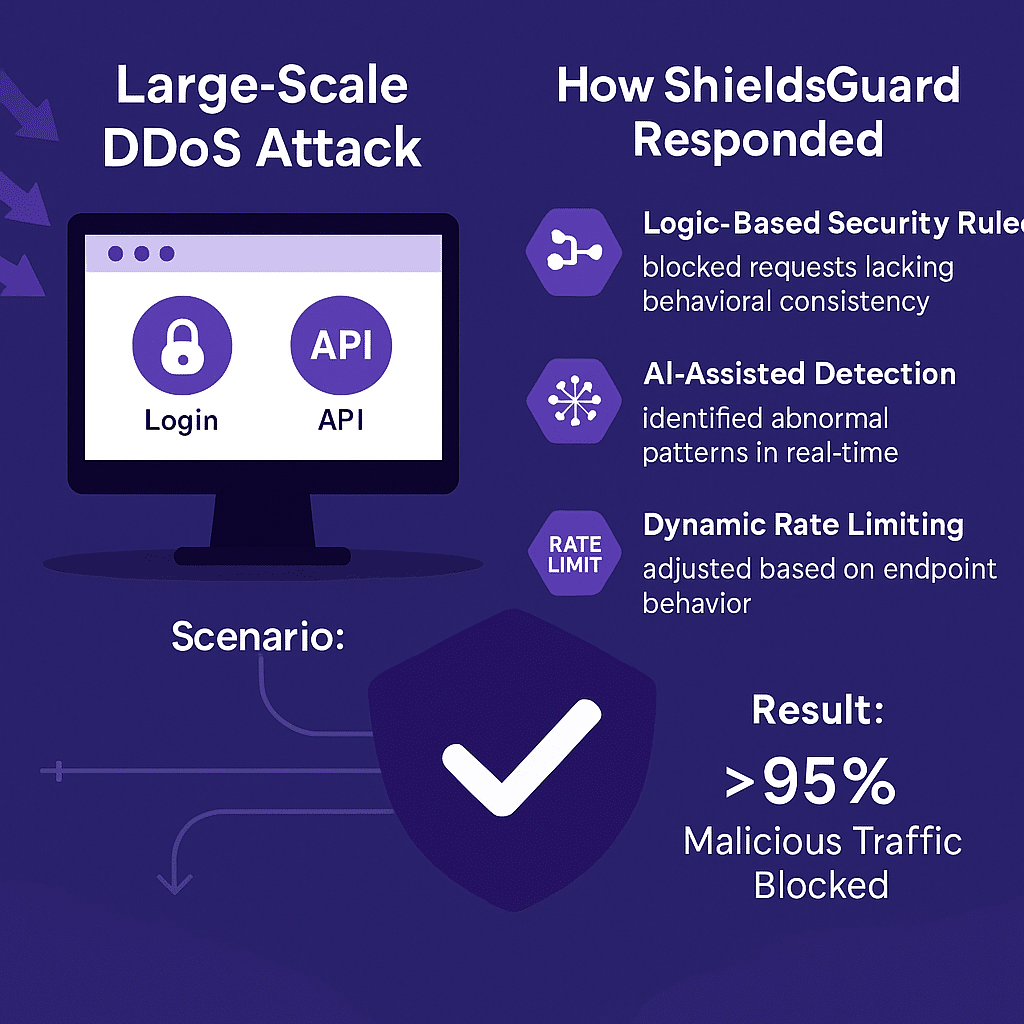
Scenario:
A large-scale Layer 7 (HTTP) flood attack targeting login and API endpoints. Attackers rotated headers, spoofed User-Agents, and bypassed conventional rate limiting.
How ShieldsGuard Responded:
- Logic-Based Security Rules blocked requests lacking behavioral consistency (e.g., missing Referer, invalid JSON keys).
- AI-assisted anomaly detection identified abnormal usage patterns in real-time and throttled connections per logic tree rather than IP alone.
- Rate limiting was dynamically adjusted based on endpoint type and behavioral score — not just raw frequency.
95% of malicious traffic was blocked before it reached application servers. No latency spike or resource exhaustion occurred.
Attack #2: DNS Reflection via Saturation of Known Ports
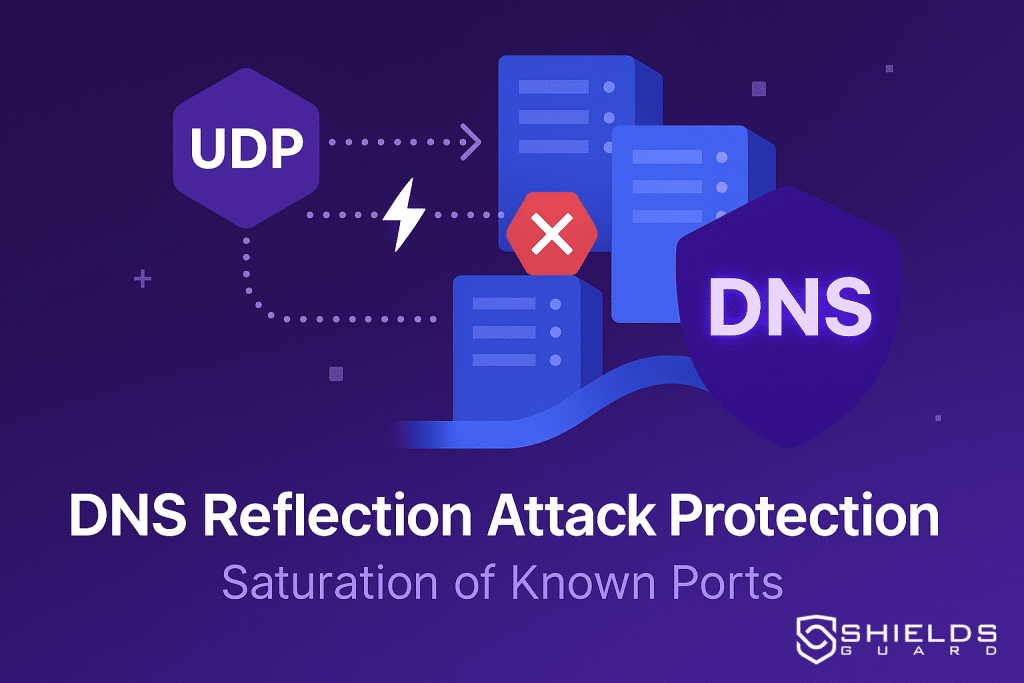
Scenario:
Attackers targeted exposed DNS services with UDP-based reflection floods designed to saturate upstream bandwidth.
How ShieldsGuard Responded:
- The network edge infrastructure (anycast-enabled) filtered volumetric traffic before routing to origin.
- AI-flagged anomalies on packet patterns triggered port-based isolation within milliseconds.
- ShieldsGuard’s DNS-aware ruleset classified and null-routed spoofed packets while leaving valid DNS queries untouched.
Zero disruption. DNS services maintained 100% uptime, with no spillover to downstream systems.
Attack #3: API Abuse through Low-and-Slow Techniques
Scenario:
Sophisticated bots attempted to bypass flood protections by sending hundreds of slow, seemingly benign API calls per session.
How ShieldsGuard Responded:
- Deep Request Inspection (DRI) identified intent behind JSON payloads using AI-based behavior models.
- Real-Time Rule Engine filtered requests that deviated from expected sequence logic, even without exceeding rate thresholds.
- Session patterns were mapped and AI-adapted rules were created on-the-fly for multi-stage detection.
All malicious sessions were dropped with no false positives. Normal users experienced no impact.
Why ShieldsGuard Works
Unlike static firewalls or cloud-only scrubbing services, ShieldsGuard integrates AI, real-time rule enforcement, and logic-based filtering at the pre-application level. Its layered defense operates across:
- Edge filtering and anycast mitigation
- AI-enhanced pattern recognition and scoring
- Custom Security Rules that evaluate methods, headers, payloads, and timing
- Instant traffic adaptation without restarts
This makes it ideal not only for blocking today’s DDoS attacks — but also for adapting as they evolve.
Final Thoughts
DDoS attacks are no longer just about volume — they’re about evasion, deception, and behavioral mimicry. ShieldsGuard doesn’t just block requests. It understands them. And when it comes to modern DDoS defense, intelligence beats brute force.
ShieldsGuard stops attacks before they start — by seeing what others miss.