In the age of high-speed automation and adaptive bots, simple rate limiting is no longer enough to protect modern applications. Attackers today aren’t just overwhelming your endpoints — they mimic real users, rotate IPs, spoof headers, and exploit business logic vulnerabilities.
While rate limiting plays a foundational role in web security, it lacks the nuance to identify intent. That’s why logic-based filtering, especially when combined with real-time defense, is essential in today’s threat landscape.
What Is Rate Limiting — and Why It Fails Alone
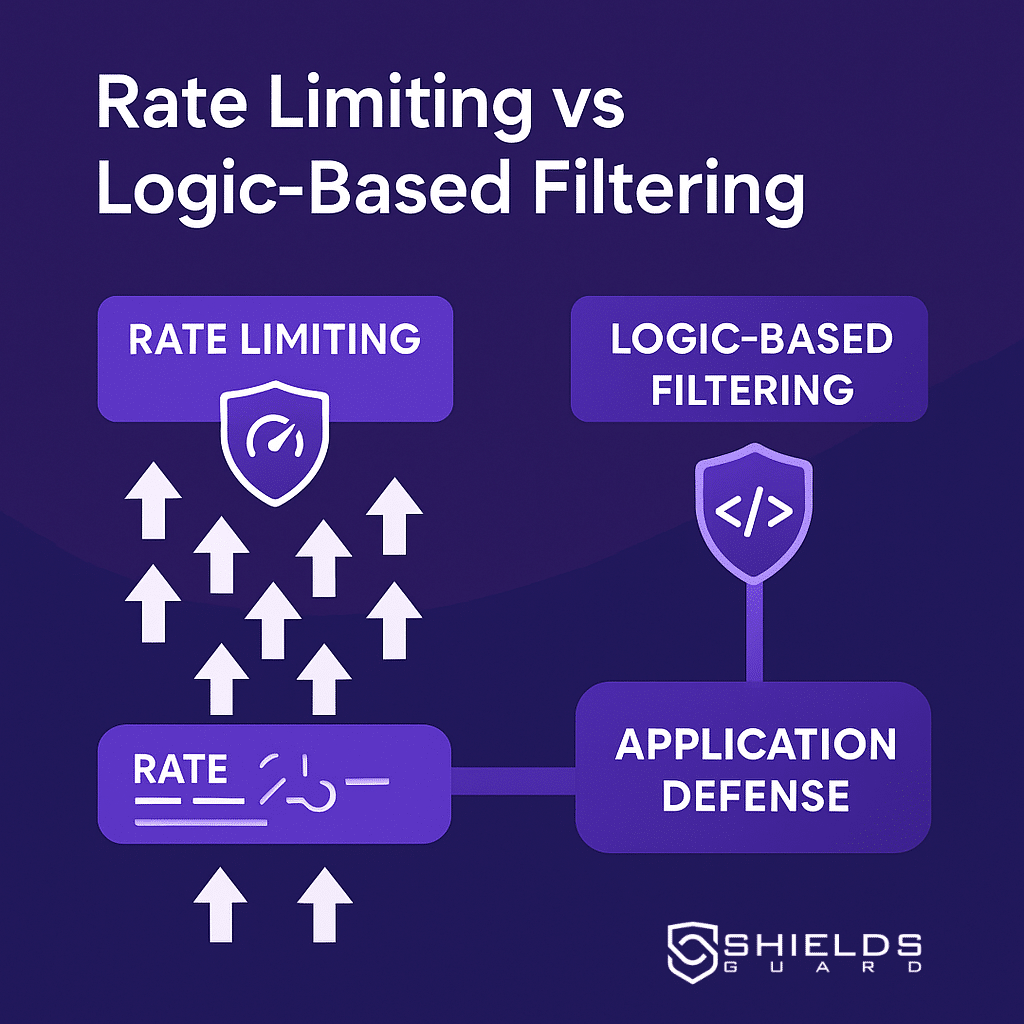
Rate limiting controls how many requests a user or IP can make over a set period. It’s great at stopping brute-force attempts and obvious floods. However, sophisticated attackers have found many ways around it:
- They use large botnets or proxy pools to rotate IP addresses.
- They perform “low and slow” attacks that stay below rate thresholds.
- They spoof headers and use human-like delays.
- They bypass basic rules using malformed or randomized payloads.
The result? Dangerous traffic that looks clean to a traditional rate limiter.
Introducing Logic-Based Filtering
This is where logic-aware filtering steps in. Rather than simply counting requests, ShieldsGuard’s Security Rules engine analyzes what a request is trying to do — and how it behaves.
Logic-based filtering looks at:
- The HTTP method and requested path
- Whether the
User-Agentor headers are missing or abnormal - The presence of automation indicators
- Specific POST/JSON body patterns
- Content-type mismatches or injection attempts
Example: Even if requests come slowly, ShieldsGuard can block a POST /login attempt if it lacks a User-Agent, has a malformed body, or contains a suspicious script — regardless of how often it happens.
Why Real-Time Defense Matters
In cybersecurity, speed matters. ShieldsGuard applies rules as requests come in, at the pre-WAF stage — before they touch your server or application. This early interception dramatically reduces:
- Server load
- WAF complexity
- Attack surface exposure
And because rules are logic-driven, they stop the intent, not just the rate.
Combining Strategies: Rate + Logic = Resilience
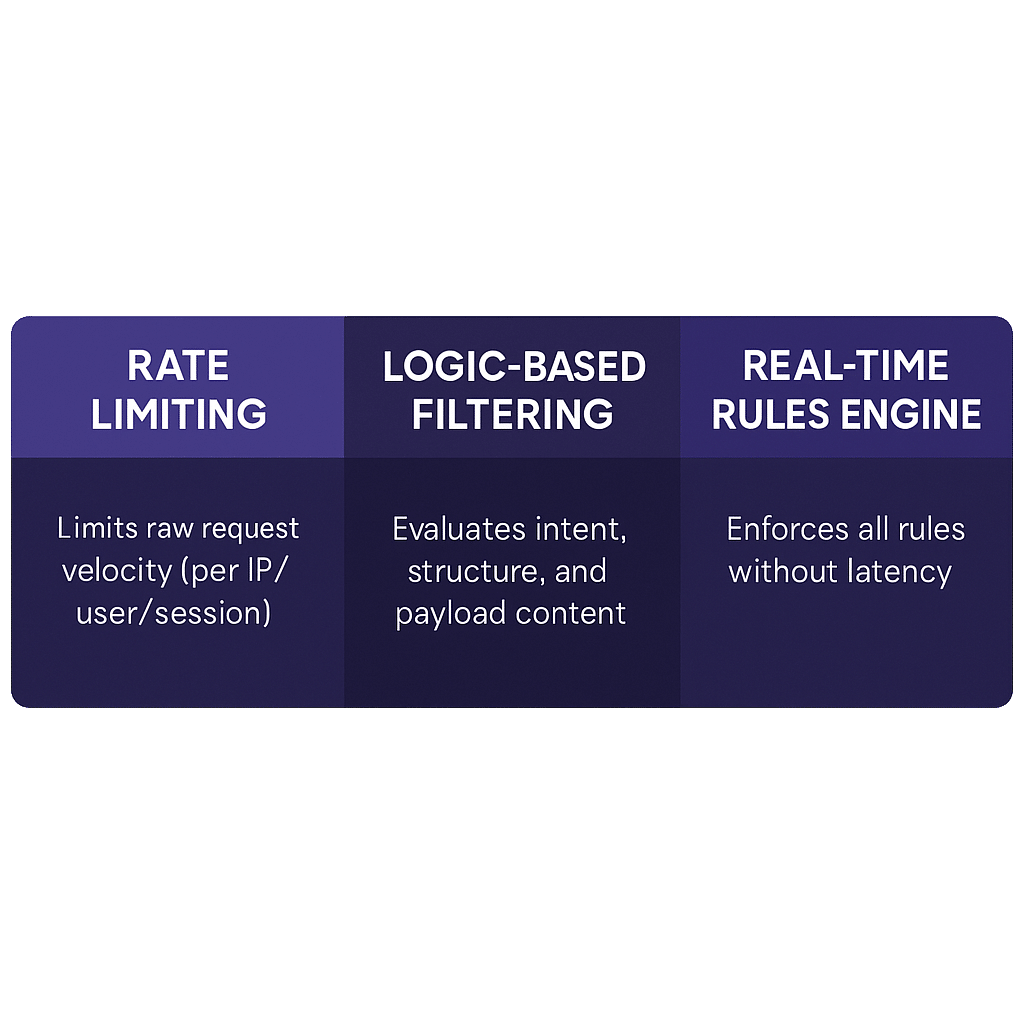
The strongest defenses aren’t built on one mechanism. ShieldsGuard enables layered protection, combining:
- Rate Limiting – Throttles repetitive behavior
- Logic-Based Filtering – Understands attack intent
- Real-Time Enforcement – Applies all rules instantly without delay
By uniting velocity controls with behavioral detection, you can shut down both obvious and subtle threats.
ShieldsGuard in Action
Here are some real-world logic filters you can define in ShieldsGuard:
- Block any
POST /api/deleteif it lacks the properX-Auth-Token - Drop login attempts where
Origindoesn’t matchReferer - Limit requests with invalid credentials to 3 tries per IP in 30 seconds
- Reject payloads with suspicious JSON values like
"action": "reset_password"missing required fields
These rules operate before your WAF — minimizing noise and false positives while optimizing performance.
Conclusion: Go Beyond Rate Limiting
Rate limiting is still valuable. But in a world of adaptive bots and complex attacks, it’s no longer enough on its own.
True defense requires understanding what a request is trying to do — not just how often it’s trying. Logic-based filtering and real-time enforcement make that possible.
With ShieldsGuard, you’re not just limiting traffic. You’re understanding it — and stopping threats smarter, faster, and earlier.